Exclusive: NATO Classified Cloud Platform Compromised
Hackers attempted to use the data in an extortion scheme, joking about altering the source code or sending it to Russian intelligence
| Emma Best | Jun 18 | 3 |
In May 2021, hackers breached a Spanish company called Everis with Latin American subsidiaries, compromising multiple datasets, including a NATO cloud computing platform, along with the associated source code and documentation. In addition to obtaining copies of the data, the hackers claimed to have deleted the company’s copies and to have had the opportunity to modify or backdoor the project. The hackers also attempted to extort Everis and made jokes about sending the data to Russian intelligence services.
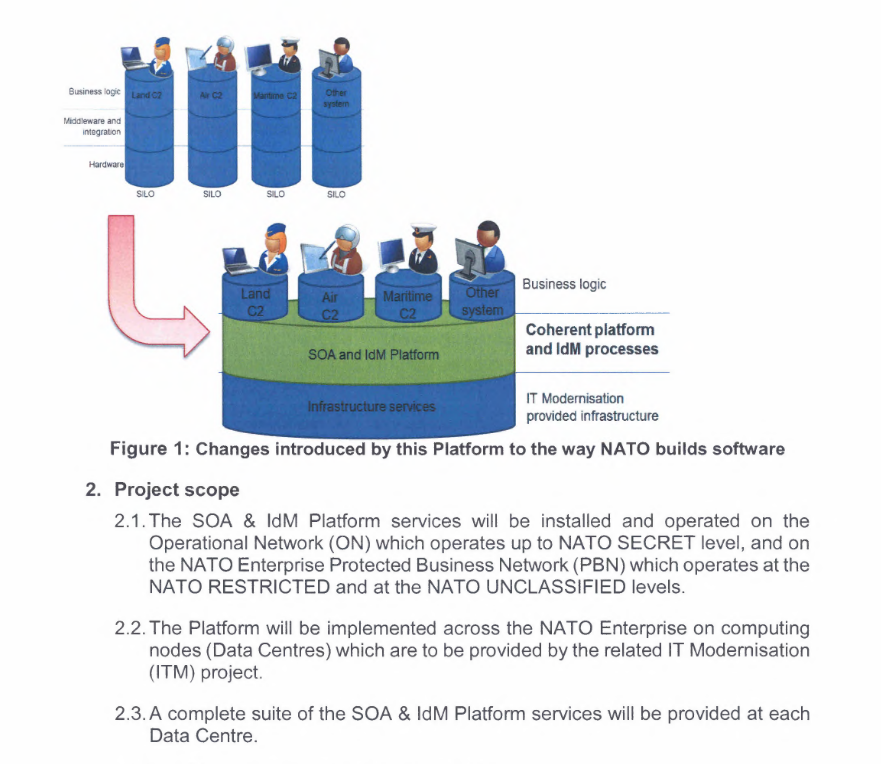
The platform, known as NATO’s Service-Oriented Architecture and Identity Access Management (SOA & IdM) Project, is one of four core projects of NATO's IT modernization efforts. The push for IT modernization, also known as the Polaris Programme, seeks to consolidate NATO’s IT infrastructure. According to Everis and a NATO UNCLASSIFIED document, SOA & IdM would have provided a central platform "responsible for security, integration, registry & repository, service management, information discovery and hosting."
According to bidding documents, the SOA & IdM Platform would be installed on data centers up to the NATO SECRET level, and would be responsible for a number of critical functions. Among other services, the platform would be responsible for logging, security, messaging, and integration with other services. Paul Howland, Polaris Programme Manager at the NATO Communications and Information (NCI) Agency described the project as “a potential game-changer for the way NATO develops and deploys its operational services in the future. It will drive innovation and reduce operational costs by ensuring much greater reuse of capabilities."
The 10.4 million EUR contract was awarded by the NCI Agency, with work beginning on it in January 2020 according to the Everis website. Everis previously with NATO in 2019, joining the signed a cybersecurity collaboration agreement for “a rapid bilateral exchange of unclassified technical information related to cybersecurity threats.” Everis has provided IT services to NATO agencies as early as 2017. Said then-Everis CEO Els Blaton, “data is the new gold; however, you do need to know what to do with all that data. Everis strives to use Big Data pragmatically for the client and analyse it safely. Given our client base in Belgium (European institutions, NATO and other international institutions, and the financial sector), cyber security is also a must. We have invested in setting up a specialised team that can roll out a cyber-security strategy for large corporations and institutions.” In 2017, Everis was also awarded a 1.5 million EUR contract for a next-generation NATO Emitter Database for electronic warfare. There’s currently no indication that these past projects or information exchanges were compromised.
According to the hackers, who described themselves as a “politically motivated threat actor” who were interested in data from Latin American subsidiaries of Everis / NTT Data. According to a note they left Everis and shared with Distributed Denial of Secrets (DDoSecrets), they were initially only interested in data relating to Latin American subsidiaries and the data they had access to through contracts. This would seem to include manifest records for LATAM Airlines, which the hackers provided to DDoSecrets [and which we are sharing with other journalists on a Limited Distribution basis due to the presence of PII]. However, after the hackers additional research on the company and seeing references to drones and defense systems, they spent more time in the company’s networks.
The hackers are, as they explained in a brief, encrypted chat with DDoSecrets, interested in peace “both on planet earth and in cyberspace.” This was, they explained, why they were happy to try to delay the Polaris Programme and cost Everis over €1 billion (it’s unclear where this figure came it, as it far exceeds the face value of the SOA & IdM contract). Despite this, they claimed the hack was “both for and against NATO” because someone could have inflicted more damage than they simply deleting and leaking their data. The SOA & IdM data provided to DDoSecrets included thousands of files of source code, documentation, and project specifications.
After receiving the data, DDoSecrets learned from the hackers’ README file that they attempted to extort Everis, offering to keep the company’s name unassociated with the LATAM Airlines leak and to not release the NATO data in exchange for 14,500 XMR. It appears the ransom went unpaid, which is consistent with Everis’ prior advice to other companies. Everis was reportedly previously targeted by ransomware in 2019, though there was no official acknowledgment from the company. DDoSecrets has made the decision not to release the data on any level due to its sensitivity, the lack of public interest, the platform’s indirect involvement in military operations, the clear potential for abuse, and its status as previously unreleased data associated with attempted extortion.
In both the README file that was originally provided to Everis and in their chat with DDoSecrets, the hackers alluded to the potential to modify the SOA & IdM software instead of deleting it and attempting to leak it. “How unfortunate it would be if someone made some changes to it before it is deployed in this secret NATO data center. I think we did them all a favor by just deleting it,” they wrote in the README file. “I hope they appreciate we just deleted all of Everis’ garbage instead of backdooring it or dropping it in the FSB securedrop,” they wrote in the chat with DDoSecrets.
In their final messages to DDoSecrets, the hackers expressed concern that that Everis was going to cover-up the breach not just from the public, but from their customers. “We have suspicion that current incident response of Everis is covering our own tracks from customer [sic].”
At the request of the hackers, their README/ransom note is being published as it was received by DDoSecrets:
Hola, chicos y chicas.
You may be wondering where your files went.
Let's introduce ourselves first. We are a politically motivated threat actor and we think it's great that one person can participate in global geopolitics armed only with a computer keyboard.
We initially were only interested in copy of data from Colombia and Chilean subsidiaries, but as we've looked at your website and saw some ridiculous words like "unmanned systems", "drones" and "defense system", we decided to spend a little more time within your network and make ourselves a copy of more data.
Here's how things will unfold.
We will publish the data of your Colombian and Chilean clients that we were initially interested in, no matter what.
We will also give you the opportunity to make a generous donation of 14500 XMR (Monero) to this address:
[Monero address redacted by DDoSecrets]
If such a donation is made within the next 3 days (until Saturday), the name "Everis" and "NTT Data" will not be linked to this leak, you will be able to respond to the incident yourself, and if the leak is traced back to your company, you will be able to control the narrative in the media. No further comment will be made from our side.
If the donation is not made, the leak will include data from other parts of the company and a detailed description of how easy it was for us to break into your network and possibly even conduct an attack on the supply chain in this small project that you are implementing for NATO and the EU-LISA.
This will include all the associated source code, documentation, and project specifications so that the information security community and the general public can judge the quality of your work, which basically tricks organizations into spending a ton of money for installing Docker into a CentOS image without any cryptographic signature to verify the integrity of that image.
How unfortunate it would be if someone made some changes to it before it is deployed in this secret NATO data center. I think we did them all a favor by just deleting it ))))
We can chat and are open to some negotiations on the offer we are making at this address:
<snip>
You will most likely need the Tor browser to access this URL, which can be downloaded here:
https://www.torproject.org/download/
Con mucho amor,
Anonymous
| 3 |

Create your profile
Only paying subscribers can comment on this post
Check your email
For your security, we need to re-authenticate you.
Click the link we sent to , or click here to log in.